Most companies think “more subdomains = more visibility.” In #cybersecurity, it’s usually the opposite.
Every new subdomain expands your #attacksurface — sometimes exponentially.
✔️ Marketing launches a new microsite.
✔️ Developers spin up a staging app.
✔️ Cloud teams test integrations.
⏩ Fast forward 12 months, and nobody remembers half of them. That’s where attackers come in.
A single misconfigured DNS entry or abandoned service can be taken over and weaponized into a more complex kill-chain— against your own domain.
🔴The Attack Playbook – A pseudo approach (being ethical of course):
1️⃣Enumerate: I'd use public tools to map out all the subdomains (here I fully make use of projectdiscovery tools).
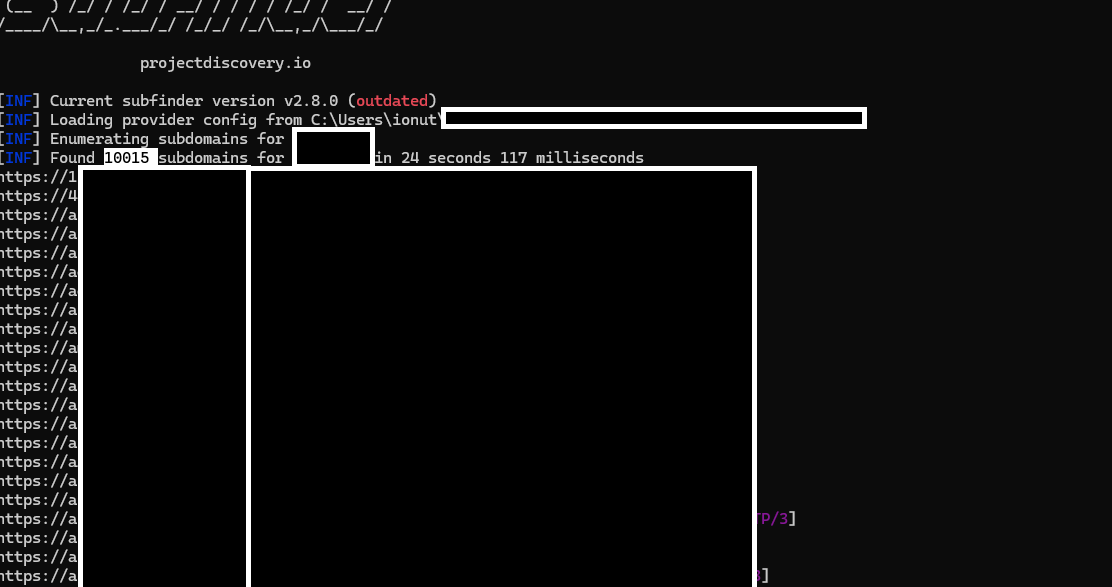
2️⃣Investigate: I'd look for CNAME records pointing to common cloud services (Azure, AWS S3, Heroku, GitHub Pages).
httpx -silent -tech-detect -status-code
3️⃣Identify: I'd filter any of those services that returned a "404 Not Found" or "No Such Bucket" error, a clear sign the resource was deleted.
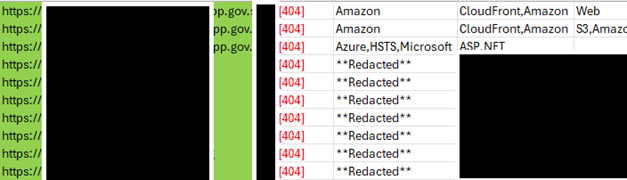
4️⃣Claim: I'd go to that cloud provider, create a new account, and register the exact same resource name. Your subdomain would now point to my server. Game over.
Next Attack Path in Kill Chain: Reputational damage (by uploading misleading content to the fresh created website), Operational Damage (replicate this scenario to hundreds of DNS Records), Financial Damage (I don’t want to generate ideas here).
Globally, security tools detect 15 expired services every 60 seconds—each one a potential subdomain takeover vulnerability waiting to be exploited.
From Vulnerability to Value: A Framework for Digital Hygiene
The threat of subdomain takeover is not an isolated issue to be patched and forgotten; it is a clear indicator of a much larger strategic challenge facing modern enterprises: the management of an ever-expanding and increasingly complex digital attack surface.
Addressing this challenge requires more than a one-time audit or a single technical fix. It demands a fundamental shift in organizational culture toward proactive, continuous DNS hygiene and a robust framework for digital asset lifecycle management.
The mindset shift? Security isn’t about how fast you grow your digital presence. It’s about how well you maintain it.